All Weeks Cybersecurity Capstone: Breach Response Case Studies Quiz Answers
Table of Contents
Cybersecurity Capstone: Breach Response Case Studies Week 01 Quiz Answers
Incident Management Knowledge Check ( Practice Quiz )
Q1. In creating an incident response capability in your organization, NIST recommends taking 6 actions. Which three (3) actions are included on that list? (Select 3)
- ‘Create an incident response policy
- ‘Develop an incident response plan based on the incident response policy
- Establish a formal incident response capability
Q2. Which incident response team model would best fit the needs of a small company that runs its business out of a single office building or campus?
- Central incident response team
Q3. True or False. An incident response team needs a blend of members with strong technical and strong soft skills?
- True
Q4. Assuring systems, networks, and applications are sufficiently secure to resist an attack is part of which phase of the incident response lifecycle?
- Preparation
Cyberattack Frameworks Knowledge Check ( Practice Quiz )
Q1. According to the IRIS Framework, during which stage of an attack would the attacker conduct external reconnaissance, alight tactics, techniques, and procedures to target and prepare his attack infrastructure?
- Attack beginnings
Q2. According to the IRIS Framework, during which stage of an attack would the attacker escalate evasion tactics to evade detection?
- Launch and execute the attack
Q3. According to the IRIS framework, during the third phase of an attack when the attackers are attempting to escalate privileges, what should the IR team be doing as a countermeasure?
- Enforce strong user password policies by enabling multi-factor authentication and restricting the ability to use the same password across systems
Q4. According to the IRIS framework, during the fifth phase of an attack, the attackers will attempt execute their final objective. What should the IR team be doing as a countermeasure?
- Thoroughly examine available forensics to understand attack details, establish mitigation priorities, provide data to law enforcement, and plan risk reduction strategies
Q5. True or False. A data breach only has to be reported to law enforcement if external customer data was compromised?
- False
Quiz 02 – Incident Management Response and Cyberattack Frameworks Graded Assessment ( Main Quiz )
Q1. In creating an incident response capability in your organization, NIST recommends taking 6 actions. Which three (3) actions are included on that list? (Select 3)
- Considering the relevant factors when selecting an incident response team model
- Establish policies and procedures regarding incident-related information sharing
- Develop incident response procedures
Q2. Which incident response team model would best fit the needs of a the field offices of a large distributed organizations ?
- Distributed incident response team
Q3. Which incident response team staffing model would be appropriate for a small retail store that has just launched an online selling platform and finds it is now under attack? The platform was put together by its very small IT department who has no experience in managing incident response.
- Completely outsource the incident response work to an onsite contractor with expertise in monitoring and responding to incidents
Q4. Which three (3) technical skills are important to have in an organization’s incident response team ? (Select 3)
- System administration
- Programming
- Network administration
Q5. Identifying incident precursors and indicators is part of which phase of the incident response lifecycle ?
- Detection & Analysis
Q6. Automatically isolating a system from the network when malware is detected on that system is part of which phase of the incident response lifecycle?
- Containment, Eradication & Recovery
Q7. According to the IRIS Framework, during which stage of an attack would the attacker send phishing emails, steal credentials and establish a foothold in the target network?
- Launch and execute the attack
Q8. According to the IRIS Framework, during which stage of an attack would the attacker execute their final objectives ?
- Attack objective execution
Q9. According to the IRIS framework, during the first stage of an attack, when the bad actors are conducting external reconnaissance and aligning their tactics, techniques and procedures, what should the IR team be doing as a countermeasure ?
- Build a threat profile of adversarial actors who are likely to target the company
Q10. According to the IRIS framework, during the fourth phase of an attack, the attackers will attempt to evade detection. What should the IR team be doing as a countermeasure?
- Analyze all network traffic and endpoints, searching for anomalous behavior
Q11. True or False. A data breach always has to be reported to law enforcement agencies.
- False
Cybersecurity Capstone: Breach Response Case Studies Week 02 Quiz Answers
Phishing Scams Graded Assessment
Q1. Which three (3) techniques are commonly used in a phishing attack? (Select 3)
- Breaking in to an office at night and installing a key logging device on the victim’s computer.Sending an email with a fake invoice that is overdue.Make an urgent request to cause the recipient to take quick action before thinking carefully.
- Send an email from an address that very closely resembles a legitimate address.
Q2. You are working as an engineer on the design of a new product your company hopes will be a big seller when you receive an email from someone you do not personally know. The email is addressed to you and was sent by someone who identifies herself as the VP of your Product division. She wants you to send her a zip file of your design documents so she can review them. While her name is that of the real VP, she explains that she is using her personal email system since her company account is having problems. You suspect fraud. What kind of attack are you likely under?
- A phishing attack.
- A whale attack.
- A man in the middle attack.
- A spear phishing attack.
Q3. Phishing attacks are often sent from spoofed domains that look just like popular real domains. Which brand has been spoofed the most in phishing attacks?
- Microsoft
- IBM
- Apple
Q4. Which feature of this email is a red flag, indicating that it may be a phishing attack and not a legitimate account warning from PayPal?
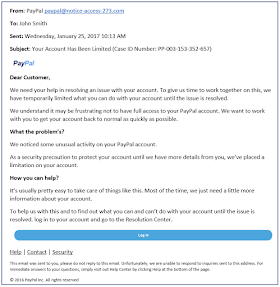
- Suspicious attachments
- There are spelling errors.
- Poor quality layout
- There is a hyperlink in the body of the email
Q5. Which three (3) of these statistics about phishing attacks are real? (Select 3)
- BEC (Business Email Compromise) scams accounted for over $12 billion in losses according the US FBI.
- 76% of businesses reported being a victim of phishing attacks in 2018.
- Phishing attempts grew 65% between 2017 and 2018.
- 94% of phishing messages are opened by their targeted users.
Q6. Which is the most common type of identity theft?
- Phone or utility fraud
- Loan or lease fraud
- Credit card fraud
- Government documents or benefits fraud
Quiz 02 – Point of Sale Breach Graded Assessment
Q1. Which group suffers from the most PoS attacks?
- Government agencies.
- Social media companies like Facebook and Instagram.
- Restaurants and small retail stores.
- Large online retailers like Amazon.com
Q2. Which three (3) of these control processes are included in the PCI-DSS standard? (Select 3)
- Maintain a vulnerability management program
- Protect cardholder data
- Require use of multi-factor authentication for new card holders
- Build and maintain a secure network and systems
Q3. Which three (3) of these are PCI-DSS requirements for any company handling, processing or transmitting credit card data? (Select 3)
- Encrypt transmission of cardholder data across open, public networks
- Use and regularly update antivirus software
- All employees with direct access to cardholder data must be bonded
- Develop and maintain secure systems and applications
Q4. Which three (3) additional requirements did the Ingenico Group recommend be used to enhance credit card transactions above and beyond the requirements found in PCI-DSS? (Select 3)
- Employee Education
- Mobile Device Management (MDM)
- Discontinue use of magnetic strip readers and cards
- Tokenization
Q5. When is credit card data most vulnerable to PoS malware ?
- After the card data has been received by the credit card processor
- While stored on the PoS device hard drive
- While in transit between the PoS device and the credit card processing center
- While in RAM
Q6. Which scenario best describes how a stolen credit card number is used to enrich the thief ?
- Credit card thieves sell stolen credit cards directly to carders using weekly dark web auctions. The carders then encode credit card blanks with the stolen numbers and resell the cards
- Credit card thieves resell stolen card numbers to dark web companies that use call-center style operations to purchase goods on behalf of customers who pay for them at discounted rates using real credit cards
- Credit card thieves use stolen credit cards to buy merchandise that is then returned to the store in exchange for store credit that is sold at a discount for profit
- Stolen credit card numbers are sold to brokers who resell them to carders who use them to buy prepaid credit cards that are then used to buy gift cards that will be used to buy merchandise for resale
Cybersecurity Capstone: Breach Response Case Studies Week 03 Quiz Answers
Third-Party Breach Graded Assessment
Q1. True or False. According to a 2018 Ponemon study, organizations surveyed cited “A third-party misused or shared confidential information…” as their top cyber security concern for the coming year.
- True
- False
Q2. How effective were the processes for vetting third-parties as reported by the majority (64%) of the companies surveyed?
- Highly effective
- Effective
- Somewhat or not effective
- Not effective at all
Q3. In the first few months of 2020 data breaches were reported from Instagram, Carson City, Amazon, GE, T-Mobile, radio.com, MSU, and Marriot. While different data were stolen from each organization, which two data elements were stolen from all of them ? (Select 2)
- Corporate financial data
- Confidential corporate strategy data
- Customer financial information
- Personal information
Q4. True or False. More than 63% of data breaches can be linked to a third-party.
- True
- False
Q5. According to a 2019 Ponemon study, which is the most common course of action for a consumer who has lost personal data in a breach ?
- Tell others of their experience
- Use social media to complain about their experience
- Comment directly on the company’s website
- File a complaint with the FTC or other regulatory body
Quiz 02 – Ransomware Graded Assessment
Q1. You get a pop-up message on your screen telling you have been locked out of your computer and that access will remain blocked until you pay a fee to have your access restored. What type of ransomware has attacked your system ?
- Blockware
- Leakware/Doxware
- Locker
- Crypto
Q2. You get a pop-up message on your screen telling you that embarrassing photos taken of you at a college party many years ago have been downloaded and will be made public unless you pay a fee. What type of ransomware has attacked your system ?
- Leakware/Doxware
- Crypto
- Locker
- Blockware
Q3. You get an email from your Internet service provider addressed to “Dear Customer” asking you to log in and verify your credentials due to “suspicious activity” detected in your account. This email is most likely trying to exploit which attack vector ?
- Malicious Links
- Remote Desktop Protocol (RDP)
- Software Vulnerabilities
- Phishing
Q4. A person you meet at a party offers to help you optimize your computer so you arrange for her to log in remotely. The next time you reboot your system, you get a pop-up message telling you all your critical files have been encrypted and you must pay a ransome to get the encryption key. What attack vector was used to exploit your system?
- Remote Desktop Protocol (RDP)
- Software Vulnerabilities
- Phishing
- Malicious Links
Q5. You fear that the security patches sent out by the vendor of one of your products may introduce changes to what you are used to so you never allow the updates. What attack vector are you setting yourself up for ?
- Malicious Links
- Remote Desktop Protocol (RDP)
- Software Vulnerabilities
- Phishing
Q6. You log into your bank and see an offer for a 0% interest rate loan. You click on the link to check out the details and suddenly your computer is locked and there is a message demanding payment in order to unlock it. Your bank’s website was hacked! What attack vector was being used to install ransomware on your system ?
- Remote Desktop Protocol (RDP)
- Phishing
- Software Vulnerabilities
- Malicious Links
Q7. True or False. Being vigilant about email you receive, links your follow and websites you visit is an effective way to keep yourself safe from a ransomware attack.
- True
- False
Q8. Which ransomware used fake Adobe Flash download websites to distribute and install ransomware?
- Jigsaw
- GoldenEye
- WannaCry
- Bad Rabbit
Q9. True or False. It is feared that in the future our cars, homes and factories may fall victim to ransomware attacks as more and more devices join the Internet of Things.
- True
- False
Next Course Quiz Answers >>
IBM Cybersecurity Analyst Assessment
<< Previous Course Quiz Answers
All Course Quiz Answers of IBM Cybersecurity Analyst Professional Certificate
Course 01: Introduction to Cybersecurity Tools & Cyber Attacks
Course 02: Cybersecurity Roles, Processes & Operating System Security
Course 03: Cybersecurity Compliance Framework & System Administration
Course 04: Network Security & Database Vulnerabilities
Course 05: Penetration Testing, Incident Response, and Forensics
